Penetration Testing
What is Pentesting?
Pentesting, also known as penetration testing, is a security assessment, an analysis, and progression of simulated attacks on an application (Web, Mobile, or API) or network to check its security posture. The objective is to penetrate the application or network security defenses by looking for vulnerabilities. These are usually weaknesses or flaws that an attacker could exploit to impact confidentiality, integrity, or availability. This goal is the same whether performing application pentesting or network pentesting. The output of a pentest is a list of vulnerabilities, the risks they pose to the application or network, and a concluding report with an executive summary of the testing along with information on its methodology and recommendations for remediation. The vulnerabilities found during a penetration test can be used to fine-tune your security policies, patch your applications or networks, identify common weaknesses across applications, and in general strengthen your entire security posture.
What is Manual Pentesting?
Manual penetration testing is an approach to security testing that layers human expertise on top of professional penetration testing software and tools, such as automated binary static and automated dynamic analysis. Pentesting software is great at discovering problems with standard vulnerability classes but is unable to detect certain design flaws.
A manual pentest performed by a skilled pentester is required to provide complete coverage including design, business logic and compound flaw risks that can only be detected through manual (human) testing.
Our approach
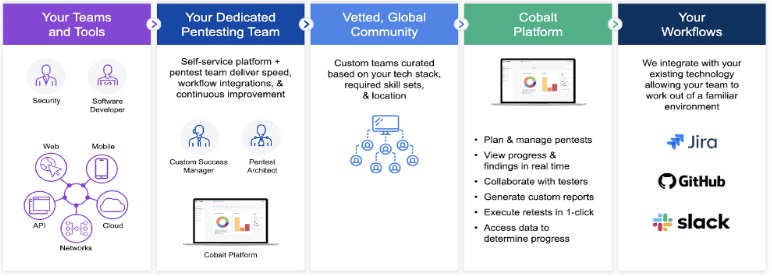
Phase 1. Preparation
The first step in the Pentesting as a Service Process is to prepare all the parties involved in the engagement. On the Customer side, this involves determining and defining the scope of the test and creating accounts on the Penetration test platform. The SecOps Team assigns a Core Lead and Domain Experts with skills that match the Customer’s technology stack. A Slack channel is also created to simplify on-demand communication between the Customer and the Pentest Team.
Phase 2. Kick Off
The second step is kicking off the pentest. This will typically involve a 30-minute phone call with the Customer and Pentest Teams. The main purpose of the call is to offer a personal introduction, align on the timeline, and finalize the testing scope.
Phase 3. Testing
The third step is where the pentesting will take place. Steps 1 and 2 are necessary to establish a clear scope, identify the target environment, and set up credentials for the test. Now is the time for the experts to analyze the target for vulnerabilities and security flaws that might be exploited if not properly mitigated. As the Pentest Team conducts testing, the Core Lead ensures depth of coverage and communicates with the Customer as needed via the platform and Slack channel. This is also where the true creative power of the Core Domain Experts comes into play.
Phase 4. Reporting
The fourth step is the reporting phase, which is an interactive and on-going process. Individual findings are posted in the platform as they are discovered, and at the end of a test the Core Lead reviews all the findings and produces a final summary report. Once the report is complete, it is sent to the customer.
The report is not static; it’s a living document that is updated as changes are made (see Re-Testing in Phase 5).
Phase 5. Re-Testing
It’s important to identify vulnerabilities in your applications, but most important is fixing the issues that are found in order to improve the security and quality of the code. Once the Customer is aware of the security issues identified during the pentest, addressing each issue happens over the course of the next few weeks and months. When the Customer marks a finding as “Ready for Re-test” on the platform, the Core Lead verifies the fix and the final report is updated.
Phase 6. Feedback
Once the testing is complete, the report has been sent to the Customer, and remediation is in the works, a Customer Success Team reaches out to the Customer for feedback. Customers initially provide feedback through a five-question survey which allows them to rate the overall process, findings, and full report. During a scheduled feedback call, Customers dive deeper into their survey responses as needed and align with the Cobalt Customer Success Team on action items and expectations moving forward. This feedback helps the Cobalt team to continue to improve the process for upcoming tests and shape the platform product roadmap moving forward.
Pentesting as a Service
Without applying a lifecycle approach to a Pentest Program, an organization is doomed to treating security as a point-in-time project rather than a continuous function. By its nature, a project has a start and end date. When the project is complete, everyone moves onto the next thing. It’s important to treat a Pentest Program as an on-going process. Step 6, the Feedback Phase, should always lead into the preparation for the next pentest whether it’s happening the following week, month, quarter, or year. Brandvakt together with Cobalt will ensure the right preparations are made for the iteration of the cycle.
Overview
Penetration testing, also known as pentesting, security pentesting, and security testing, is a form of ethical hacking. It describes the intentional launching of simulated cyberattacks by “white hat” penetration testers using strategies and tools designed to access or exploit computer systems, networks, websites, and applications. Although the main objective of pen testing is to identify exploitable issues so that effective security controls can be implemented, security professionals can also use penetration testing techniques, along with specialized testing tools, to test the robustness of an organization’s security policies, its regulatory compliance, its employees’ security awareness, and the organization’s ability to identify and respond to security issues and incidents such as unauthorized access, as they occur.
As a simulated cyberattack, ethical hacking techniques help security professionals evaluate the effectiveness of information security measures within their organizations. The pentest attempts to pierce the armor of an organization’s cyber defenses, checking for exploitable vulnerabilities in networks, web apps, and user security. The objective is to find weaknesses in systems before attackers do.
When do you need Pentests?
Whether getting acquired or acquiring another company, you will find that security assessments have become an integral part of the due diligence process. 100% of executives and advisors in a 2019 (ISC)2 survey said security audits have become standard practice in M&As. Pentests are a common component of these audits, both as a point-in-time snapshot and as part of a continuous testing program.
If your auditor doesn’t ask for a pentest, chances are your customers will. Digital services have created a complex network where one successful breach can impact multiple companies connected to the target, as evidenced by the FireEye and SolarWinds incidents in late 2020. As a result, businesses are increasingly concerned about their vendors’ commitment to security and before they sign, they request documents such as a SOC 2 report or a pentest report issued in the past 6 months.
Clearly, the pressure is on for cybersecurity. To mitigate risk and mature their programs, teams are increasingly diversifying their approaches. One example is the combination of automated security tools and manual pentests. When configured correctly, scanners can capture malware signatures, coding errors, and suspicious behavior patterns. Pentests can act as an additional layer of defense, validating these tools’ accuracy and searching for more complex flaws that require creative thinking: business logic flaws, authorization inconsistencies, chained exploits, and race conditions.
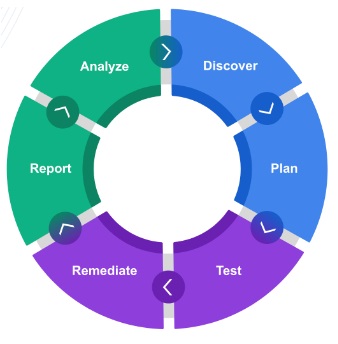
How it works
Brandvakt offers Pentesting-as-a-Service together with Cobalt. Our approach is an agile approach with a short initiation time, usually 24-48 hours. Once the scope has been defined, the penetration test occurs over a set of two weeks. In contrast to traditional penetration testing, you do not have to wait weeks for the report but can rather follow along in a dashboard as the penetration testing occurs and as vulnerabilities are unveiled. Along with the discoveries, recommendations on how to remediate the problems are provided.
Our penetration testing is an agile approach following the following steps Plan -> Test -> Remediate -> Report -> Analyze -> Discover.
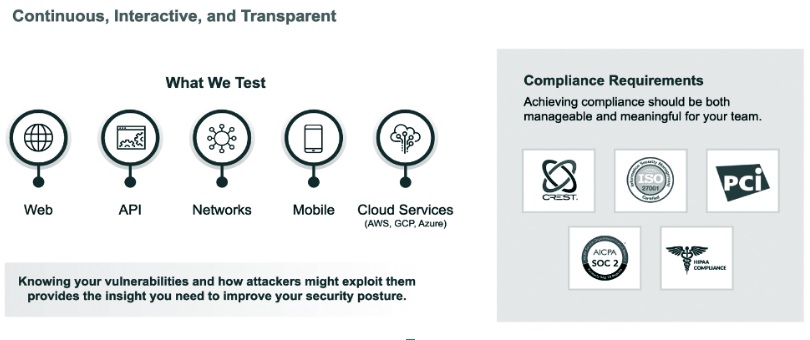
What can we test?
Web Application Pentest
The internet is an essential aspect of many day-to-day tasks. Millions of people use websites and applications to shop, bank, and browse securely. As web applications have become increasingly popular, they are under constant threat from hackers, viruses, and malicious third parties.
As many web applications store or send out sensitive data, the apps must be secure at all times, especially those used by the public.
Web application pentesting works as a preventative control measure, allowing you to analyze every aspect of your web application’s security.
Experts follow a web application pentesting best practices and with the goals of:
- Test the effectiveness of existing security policies
- Identify unknown vulnerabilities
- Determine the most vulnerable areas for an attack
- Test all publicly exposed application components (routers, firewalls, and DNS)
- Find any loopholes that could be exposed to data theft
Cloud Config Review
The primary and fundamental difference in cloud penetration testing is that your organization doesn’t own the underlying hardware that your systems/applications/services are running on. So you’ve got to make sure that you have permission prior to testing your cloud infrastructure or having a third-party test it. In some cases, this is really simple, as many hosting providers don’t require permission anymore to perform network-level penetration testing of your public facing hosts (e.g. Azure, Digital Ocean, Google), as long as the testing doesn’t include any denial-of-service (DoS) aspects.
Code Assisted Pentest
Pentests are typically performed from a “black box” or “zero-knowledge” perspective; meaning the security pentesters have limited to no prior knowledge about the implementation details of the target, in-scope application. With code-assisted, gray-box penetration testing, Our pentesters have access to the source code of the application, effectively enabling the team to use the code alongside testing activities as a means to gain a thorough understanding of the target application and enhance the accuracy of the discovered findings. However, our code assisted pentest is not a code review since it is only used to analyze attack vectors.
Don’t hesitate to reach out to Us directory so that we can in more depth discuss penetration testing as a service and how the Cobalt platform works.
Types of Software Testing
Black Box: No prior access is given during an external network pentest unless explicitly outlined in the scope.
White Box: Specific access is given during an external network pentest.
Gray Box: No access is given to start, but some access is given after certain tests are performed.
Further, these details can be included in the scope of the desired pentest with gray box and white box testing:
- Network diagrams
- Infrastructure diagrams
- Accounts (even temporary accounts for pentests)
- User information
Any information provided about the system being tested is useful for pentesters. The more opportunity and ability there is to figure out the software that someone’s web server is running, the more effective it is to find exploits specifically related to that version of the software rather than trying a variety of exploits to see what sticks.
We can meet customers where they want us to be. However, if customers are looking for maximum impact and/or a white-box test, here’s what we recommend when preparing the test’s scope:
- Determine the assets to test, such as which parts of the external network
- Determine the IP addresses that go with those assets
- Present those IP addresses as the scope
It’s important to ensure the provided IP addresses actually belong to the company, and also alert any third-party vendors related to those assets. To increase the value of external assessments, monitoring public IPs from which attacks are sometimes conducted can be helpful to better identify and respond to future attacks.
When it comes to the typical list of things we normally check during an external network pentest, they follow frameworks and best practices such as OWASP, ASVS, or OSSTMM. Typically port scanning activities are performed, followed by the search for web servers. Determining the software and version in use for each service is also helpful in identifying misconfigurations or vulnerabilities.
API Pentest
The lack of a clear protocol makes application security assessments of microservice APIs somewhat precarious, since the typical go-to web security assessment tools, prescribed security assessment methodologies, and general penetration tester experience may not include coverage or interaction know-how for a particular microservice API offering or operational behavior.
API Penetration testing involves all processes of checking for vulnerabilities and building strong endpoints in your APIs. One of the most common web application threats is API abuse, which can cause hindrances to the smooth running of any digital industry.
API penetration testing is very similar to web application penetration testing and so the API pentesting methodology is based on the same foundation — the OWASP Top 10, the OWASP ASVS, and the OWASP Testing Guide. Cobalt tests web-based APIs, REST APIs, and mobile APIs. Our pentesters analyze the target API to determine which authentication type is used, study API structures, understand request methods, responses, roles, and exploit bugs on a real production API or an API in a staging environment.
External Network Pentest
It’s important to know your organization’s vulnerabilities and how attackers might exploit them. External network pentesting is one way to do so, by actively assessing the security of an organization’s perimeter infrastructure that is directly accessible from the internet. This is done to pinpoint potential areas of opportunity for attackers to gain sensitive information and compromise business-critical infrastructure.
External networks include the server, the VPN login, a webmail portal, and any portals that can be accessed from a web browser. During an external network pentest, Our pentesters use real-world attack vectors and tools to attempt to compromise external systems and gain access to sensitive information or systems.
Mobile Application Pentest
Our pentesters go beyond simply looking at common API and web vulnerabilities. Our testers examine the risk of a mobile application by leveraging OWASP Mobile Top 10 and other methodologies to assess security.
Security has always been a major concern for businesses, and this concern is even greater when it comes to mobile applications. Today, almost every leading brand or product has a mobile app to connect with their customers more easily.
More users than ever, rely on mobile applications for a majority of their digital tasks over traditional desktop applications. These applications have access to large amounts of user data, much of which is sensitive data and must be protected from unauthorized access.
From a pen tester’s perspective, there is a growing need for skilled mobile pentesters. Mobile applications is an important attack surface to cover, and although all popular mobile platforms (iOS & Android) provide their own set of security controls designed to help the developers build secure applications this is often left to the developer to choose from a variety of security options. If not implemented properly, or left misconfigured, they introduce security loopholes in an application.
