Vulnerability Management
Introduction
The process of identifying, evaluating, treating and reporting on security vulnerabilities is typically referred to as ‘vulnerability management’. Having a sound vulnerability management program in place is vital for organizations to be able to prioritize possible threats and to limit the “attack surface”.
Hacktivists and cybercriminals look at exploiting known vulnerabilities to cause reputational or financial damage to your organization. With a Vulnerability Management program in place, effective safeguards can be put in place to protect systems, networks, and data by effectively and continuously closing existing security gaps before they are exploited.
Overview
A typical approach is to deploy vulnerability management tools such as Tenable Nessus, which scan enterprise networks to identify and report on weaknesses that intruders may exploit. Brandvakt works closely with industry leaders such as Tenable to provide the right solutions to quickly and effectively protect against known threats and vulnerabilities.
We can help your enterprise to understand your risks, and know which vulnerabilities you might be exposed to and in what order they should be fixed.
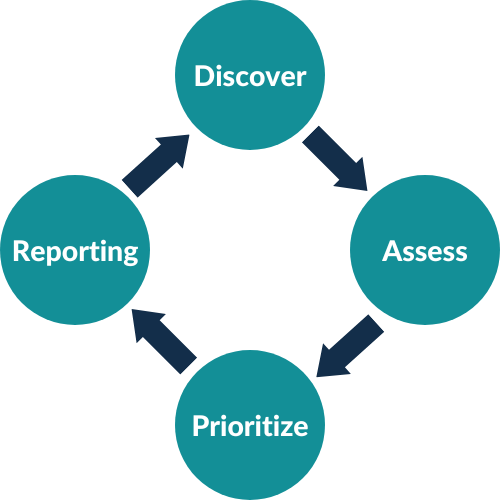
How it works
Specifications
1. Identify vulnerabilities
The first stage of the management process requires identifying which vulnerabilities might affect your systems. Once you know which vulnerabilities or vulnerability types you are looking for, you can begin identifying which ones exist.
This stage uses threat intelligence information and vulnerability databases to guide your search. It also often uses vulnerability scanners to identify affected components and create an inventory for use in patch management. Brandvakt has partnerships with industry leading vendors such as Tenable to offer effective and powerful capabilities to identify vulnerabilities.
As part of this phase, you want to create a full map of your system that specifies where assets are, how those assets can potentially be accessed, and which systems are currently in place for protection. This map can then be used to guide the analysis of vulnerabilities and ease remediation.
We can help your enterprise to understand your risks, and know which vulnerabilities you might be exposed to and in what order they should be fixed.
2. Evaluating vulnerabilities
After you have identified all possible vulnerabilities in your system, you can begin assessing and evaluating the severity of the threats. This evaluation helps you prioritize your security efforts and can help reduce your risks more quickly.
If you start remediating the most severe vulnerabilities first, you can reduce the chance of an attack occurring while you’re securing the rest of your system. When evaluating vulnerabilities, there are several systems you can use to establish the risk of a vulnerability being exploited.
An industry standard is the Common Vulnerability Scoring System (CVSS). This is a standardized system used by many vulnerability databases and researchers. CVSS evaluates the level of vulnerability according to inherent characteristics, temporal traits, and the specific effect of the vulnerability to your systems. The challenge with CVSS is that once a risk level is assigned, it is permanent, so it’s important to include other factors from threat intelligence and your own business risk information, in order to determine prioritization.
With Tenable, Brandvakt can offer coverage for more than 71.000 vulnerabilities – which is the industry’s most extensive CVE and security configuration support to help you understand all of your exposures.
3. Remediating vulnerabilities
With a prioritized vulnerability management plan in place, you can begin your remediation efforts. During this phase, you may also want to increase monitoring or reduce access to areas identified as at-risk. This can help prevent successful exploitation of vulnerabilities until you can apply patches or permanently increase protections to those areas.
Brandvakt helps you combine vulnerability data, threat intelligence and data science for easy-to-understand risk scores to quickly assess risk and know which vulnerabilities to fix first.
After vulnerabilities are addressed, make sure that you verify successful remediation. Penetration testing is useful for this, as it can help you gauge the effectiveness of your fix. It can also help you ensure that new vulnerabilities weren’t created during your remediation efforts.
4. Reporting vulnerabilities
Reporting vulnerabilities after remediation may seem unnecessary, but it can help you improve your security and responses in the future. Having a record of vulnerabilities and when those issues were fixed shows accountability for security and is required for many compliance standards. It can also be useful when investigating future events. For example, if you find evidence that an attack has been ongoing, you can look at your patch histories to narrow down possible routes and times of entry.
Additionally, reporting on your vulnerability management process creates a baseline for future efforts. This can help you improve the effectiveness of future efforts, and can help you avoid the inclusion of new vulnerabilities by reflecting the lessons you’ve learned.
Effective Vulnerability Management Program
Developing an effective Vulnerability Management program can take some time, and you are unlikely to get it exactly right on the first try. Brandvakt provides the services to ensure a smooth establishment of a vulnerability program based on best practices forming the foundation from start reducing the number of refinement and iterations needed.
